There’s a ton of different ways to implement a cyber security strategy these days. Various vendors and suppliers have their own products and methods. With all the choices out there, the Essential Eight cyber strategy is a good place to start.
With the Essential Eight, you’ll get a at least a starting point as a basis for your cyber security strategy. Fortunately, it’s easy to implement, it’s not going to break the bank and it will co-exist with other cyber security strategies.
The Australian Signals Directorate’s cyber security teams have developed the Essential Eight program. The Essential Eight is a baseline strategy that your business can deploy as a starting point to mitigate against cyber incidents.
What is the Essential Eight Cyber Strategy?
The essential eight is a set of initiatives that you can implement within your business. Once you’ve deployed the Essential Eight, it’s going to make it harder for the ‘Bad Actors’ to get access to your environment from the outside.
The Essential Eight strategies are:
- Application white listing
- Application patching
- Microsoft Office macro configuration
- Application hardening
- Restricting administration privileges
- Operating system patching
- Multi-factor authentication
- Daily backups
To implement many of the ASD’s initiatives, you may not need to put in a lot of effort. You may have the tools or skills in house today.
You can get more detail on the Essential Eight from the Australian Signals Directorate website.
Application Whitelisting
Application white-listing allows a configured list of applications to run within your environment. It’s a basic premise that anything that’s not in the white list is blocked and can’t run.
Application white listing essentially stops the execution of unknown applications dead in their tracks. Chances are that if you don’t know what an application is you don’t want it to be running on any machine.
This will trap most malware, ransomware and command and control agents.
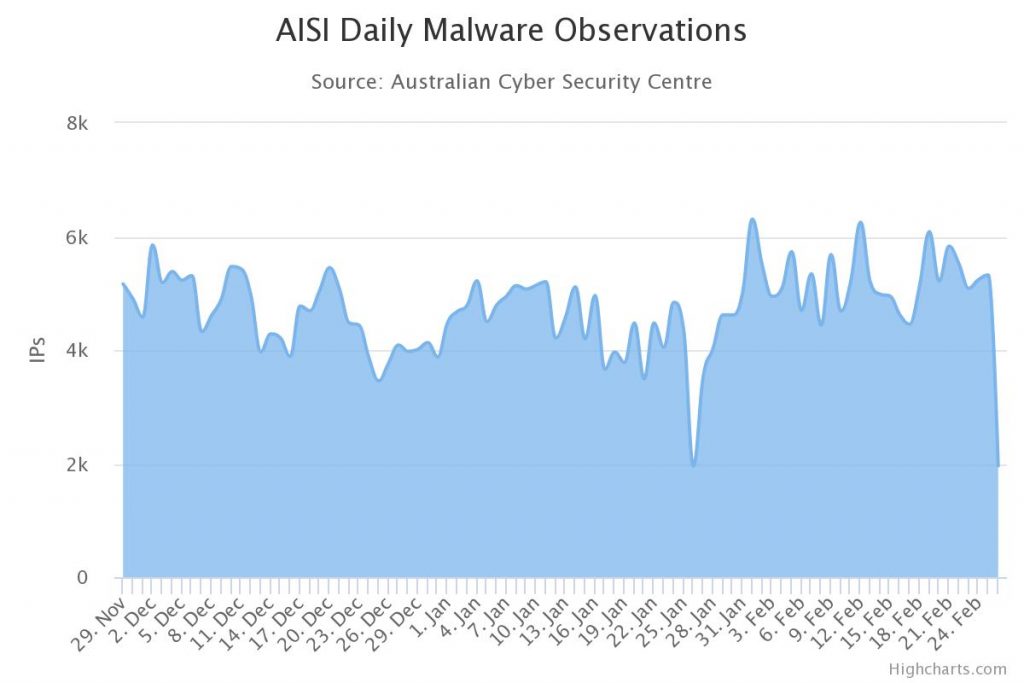
The chart below show the number of reports infections from malware. These numbers are based on reports by Australian Internet Security Initiative members. This data is updated daily and can be found on the ASD website.

To implement application whitelisting you need to build a list of approved, or trusted, applications that you run within your business. This includes all the EXE, DLLs and scripts across your platforms.
It can be a bit of a task to identify absolutely everything. Once you’re done, you are going to need a process built into your Change Management functions to maintain the list and keep it up to date.
Enforcing the whitelist can be done through Active Directory, some anti-virus applications, such as Trend Micro, and other next-generation endpoint security products like Palo Alto’s Traps.
Application Patching
Keeping you applications patched and updated should be high on your priority list. Security vulnerabilities within your applications are a risk that your IT team should be able to easily manage.
Security vulnerabilities in applications can be used to execute malicious code on systems.
Applications that you should be patching don’t just include your core business apps. You should also maintain the most secure versions of your web browsers, Microsoft Office, Adobe Reader and Java. That’s on a short list though. You’ll likely have many more.
Application vulnerability details are often released by the application vendor.
For any applications that you have that are end of life or not longer supported by a vendor, the ASD recommends, as so do we, to upgrade or replace the application with one that is supported.
Deploying the latest patches for your applications is going to vary from vendor to vendor. Oftentimes, IT teams find it difficult and time consuming to patch applications. It could also be expensive for some companies to deploy a central system for managing the deployment and upgrade of applications.
These are hurdles you need to find a way to overcome. You may need to source a 3rd party provider to help you with your patching regime.
Your applications are important and your staff uses them every day. You should find a way to keep them up to date if you don’t have one already.
Microsoft Office Macro Configuration
Microsoft Office macros have long been a sneaky, and effective, way of delivering malware.
Over time, Microsoft has changed the way macros are handled with in its Office suite and applications like Word and Excel.
The simple fix is to disable the running of Macros through Microsoft Office for documents that have been sent via the Internet.
Taking it that little bit, the ASD recommends tightening up controls to only allow macros to run from documents stored in trusted locations, such as you’re own environment.
Locking down the use of Office macros should be considered. Sometimes, this isn’t practical. You may need to share macro enabled documents with your clients and suppliers.
At the very least, the ASD recommends that you lock down your Office macros so that your staff are prompted to allow the macros to execute each time.
To marry up with the Maturity Level 1, the ASD recommends that you lock down your systems to prevent any staff from changing the security settings permanently on their systems.
Like application whitelisting, securing and locking down the use of macros through Microsoft Office can be handled with Intune or Group Policy.
User Application Hardening
You’ll find many security vendors citing the human element as the weakest link in the cyber security chains. Sometimes people are gullible, don’t pay full attention or simply don’t know any better.
Hardening applications on desktops and laptops will go along way to reducing this risk.
With the Essential Eight, locking down applications that your staff are using, such as web browers is simple but smart thing to do.
To start, you want to block Flash from running in our browser by default. Disabling ads and Java on the Internet can help with attacks from malicious sites. You can read about drive-by attacks here.
On the desktop side, see what you can do for each of your applications. For Microsoft Office you can disable unneeded features such as Object Linking and Embedding (OLE).
Restricting Administrator Privileges
Sure, this one sounds pretty simple but you might be surprised to learn how many user accounts in your business have elevated rights.
In a recent review of one prospect’s Active Directory, we found 112 Domain Administrators. 8 of those were from staff that had recently left and 52 were external contractors.
Giving people more access to systems and data than they need to do their jobs poses a very real security threat. With the right level of access, compromised accounts can be user to corrupt or exfiltrate data.
You can implement various policies around access control that should outline who has access to the various systems and data you have. An Access Control Policy will also detail what roles and access that your IT teams need to build to protect your business without hampering your staff from carrying out their daily tasks.
The Essential Eight Cyber Strategy Says Patch Your Operating Systems!
Again, another no-brainer directive from the ASD here. This is advocated by everyone. Even so, many businesses who think they are patching their systems are often out of date.
The Essential Eight cyber strategy has various levels of risk that should be guarded against depending on the system.
For example, any systems that are deemed as an ‘extreme risk’ to the business if they were compromised should have their operating systems patched within 48 hours of any vulnerability that has been identified.
Our advice is to review your patching policy. While the ASD might suggest you patch your systems withing 48 hours of an ‘extreme risk’ vulnerability, sometimes this isn’t practical.
Make sure you patching policy includes what to patch, when and how often.
Deploy Multi-Factor Authentication
With the rapid take up of cloud applications and a work from anywhere philosophy, you need a new approach to information security. A simple username and password combination is no longer enough to protect your data.
Credential harvesting attacks are increasing. The media is full of articles about password theft.
The risk of using simple username/password combinations is that people often use the same password in multiple locations.
By implementing a second factor to control access to applications and data, you are making it so much harder for those bad actors to access your systems and data.
Perform and Check Your Backups Daily
It should go without saying that every business should be backing up their data regularly.
Backups, stored in a different location, are one of the best securities of data loss and corruption.
Make sure you are backing the data you need as often as required. Also, make sure you test regularly that you can recover the data you’ve backed up.
Are You Ready for the Essential Eight Cyber Strategy?
It’s likely that you’ll be able to get started on implementing the ASD’s Essential Eight within you environment today.
You should be patching all your systems, you should have regular backups of your data. If you don’t, it’s easy to start now.
Some of the Essential Eight might prove challenging or you many not have the resources or expertise to implement the strategies. If you need help, advice or some help to get you started in the right direction, let us know.